CI/CD with Tekton
Tekton is an open source framework for creating CI/CD systems. With the help of Tekton, developers can continuously build, test and deploy their applications. Tekton can be used as a CI/CD system in Kubernetes environments. Tekton is also used in OpenShift as the OpenShift Pipeline Operator.
Trigger and event listeners
In conjunction with a source code management system (SCM), such as Bitbucket, GitLab or GitHub, there is often a requirement that certain events in the SCM should trigger the start of a Tekton pipeline. For example, if a pull request is integrated, the master branch should then be built and the application should be deployed.
Tekton provides the resources Trigger and EventListener for these scenarios. The integration with the SCM usually takes place via webhooks. An event in the SCM triggers the webhook, and this transfers the information about the event in the form of a payload to an endpoint that is connected to a specific event listener. The information from the event is extracted in the trigger and then used to start a specific Tekton pipeline. The following graphic is taken from the official Tekton documentation and illustrates the interaction:
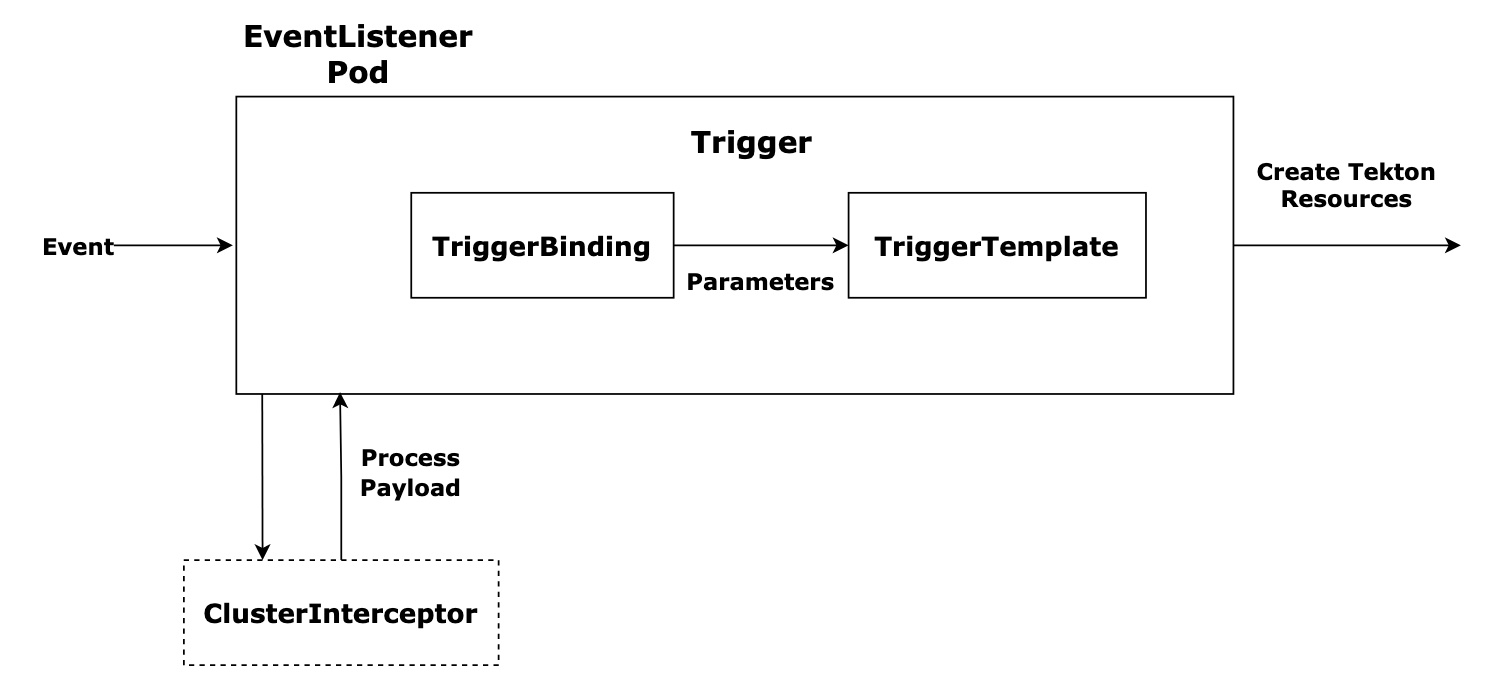
Interceptors
The validation, filtering and transformation of the event information is handled by so-called Interceptors. Tekton already provides ready-made interceptors for Bitbucket, GitLab and GitHub, which facilitate integration with these SCMs. The following example shows the use of the Bitbucket Interceptor:
interceptors:
- ref:
name: bitbucket
params:
- name: secretRef
value:
secretName: bitbucket-server-secret
secretKey: secretToken
- name: eventTypes
value:
- repo:refs_changed
The interceptor checks that the event information received in the webhook request has been signed by Bitbucket based on the configured secret (Details). This ensures that the event information has not been manipulated unintentionally. The eventTypes parameter can be used to specify the events for which this interceptor should be active. Different events can be configured depending on the SCM and the associated interceptor. For example, the Bitbucket event repo:refs_changed corresponds to a push of a commit to a repository (Details).
In practice, you quickly reach a point where the configuration via the existing events (eventTypes) alone is no longer sufficient. For example, if you only want to start a pipeline when the commit has been pushed to a specific branch and not, for example, when a tag has been pushed, or when a branch has been created but not when the branch has been deleted.
CEL interceptors
The predefined interceptors can be extended with the help of a CEL interceptor. The CEL interceptor enables, among other things, the filtering of event information. The event information is available in the payload in JSON format. With the Common Expression Language CEL, the payload can be filtered as follows, for example:
interceptors:
- ref:
name: bitbucket
params:
- name: secretRef
value:
secretName: bitbucket-server-secret
secretKey: secretToken
- name: eventTypes
value:
- repo:refs_changed
- ref:
name: cel
params:
- name: filter
value: "body.changes[0].type == 'ADD' && body.changes[0].ref.type == 'BRANCH'"
The filter contains a Boolean expression that is only evaluated to true if a commit has been pushed to a branch.
Summary
In conjunction with the integrated interceptors for common SCMs, a CEL interceptor can be a useful addition to decide whether a Tekton pipeline should be started or not based on the event information in the payload. Simple CEL-based expressions allow for individual fine-tuning.
